Interested in seeing our payment products in action? Request a Demo
Leverage technology for the perfect integrated solution
One of the most crucial aspects of choosing a payment tool is its ease and speed of setup. With the availability of our easy-to-integrate APIs and SDKs, developers can now utilize pre-built code libraries to connect new technologies to their applications. Our comprehensive documentation and step-by-step guides simplify the setup process, enabling you to start within minutes. If you want to monetize payments effortlessly and enhance your app with new features, explore our APIs and SDKs.
Valor offers shopping cart integrations to adapt to the specific needs of any business. With easy-to-implement solutions, these integrations ensure that online retailers can quickly align their cart functionality with their brand identity, providing customers with a familiar and coherent shopping journey.
Give your store the edge with Valor Pay’s powerful integrations. Whether you’re using a hosted cart like BigCommerce or self-hosted platforms like Magento or OSCommerce, our plugins and APIs are built to plug right in – no coding headaches.




A fast, secure plugin for your WordPress-powered store.




Feature-rich payments built for scale.


Payments made simple, setup made simpler.



Embed payment forms directly on your site or use hosted pages – your choice.

A fast, secure plugin for your WordPress-powered store.

Plug-and-play payment integration with zero complexity.

Feature-rich payments built for scale.

Payments made simple, setup made simpler.

Secure transactions and flexible controls.
Personalize any business payment solutions with Valor’s user-friendly SDKs.
These tools are designed to drive business growth and streamline operations.
Sync transactions, invoices, and customer data effortlessly
Connecting QuickBooks to Valor takes just a few clicks. Log in and authenticate, and a green checkmark will confirm a successful integration.
Businesses can generate, update, and track invoices directly within the Virtual Terminal and QuickBooks.

Every transaction processed through the Valor Portal—whether it's a sale or an e-invoice—instantly reflects in QuickBooks. No more manual reconciliations or missing entries.

Generate detailed transaction reports, filter by date or device, and export data instantly giving busineses full visibility into their financials.

Effortlessly pull customer details into Valor Vault or QuickBooks and sync product catalogs between the two. This makes selling products, managing inventory, and transitioning platforms seamless.

Why overcomplicate payments when ACH can do it all? With ACH integration in Valor PayTech’s Virtual Terminal, businesses can move money securely, slash processing costs, and keep transactions running like a well-oiled machine—minus the headaches.
Say goodbye to high fees and hello to streamlined payments.

Encrypted, authenticated, and fully approved.

Give customers more ways to pay with direct bank transfers—no cards required.

Track and manage payments effortlessly through Valor’s ACH module.

Semi-integration is a checkout method that integrates payment processing and point-of-sale software into a secure and organized network configuration. It enables stores to accept Chip/EMV credit card and debit card payments while managing inventory changes, returns, voided transactions, and other payment functions.
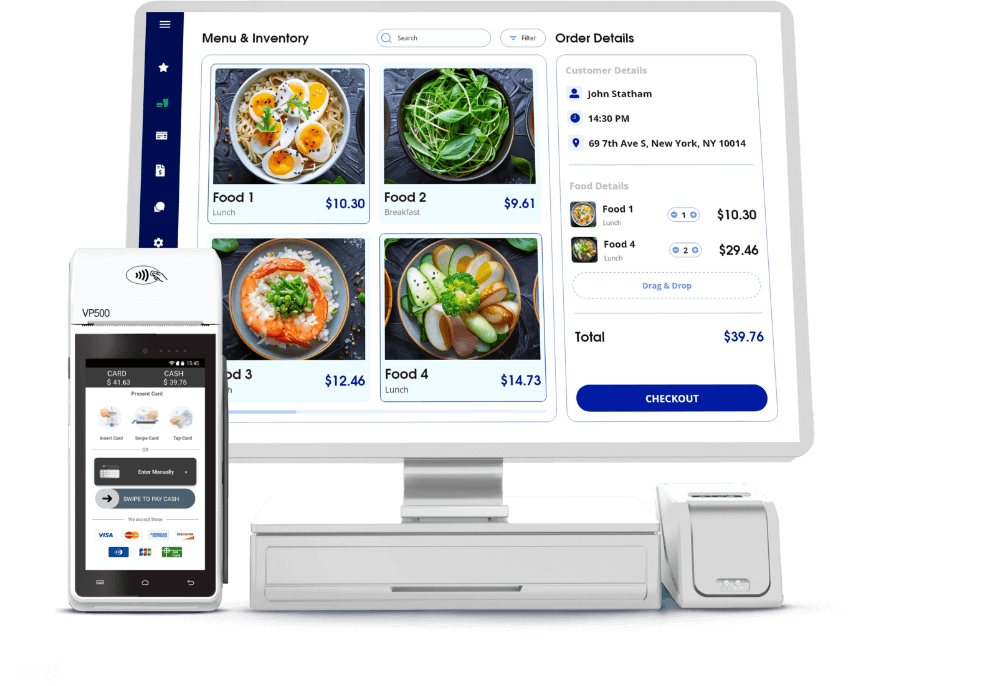
Semi-integrations help users to easily integrate one POS desktop or device with multiple POS terminals and support several processors, allowing ISVs and Independent Software Organizations (ISOs) to develop a single semi-integrated specification that can support multiple devices and processors. This provides enormous flexibility for businesses and saves time.

EMV certifications can be expensive and time-consuming. However, with semi-integration, these certifications are completed by the processor and payment gateway. The most typically required is a simple device integration script or unit testing, significantly reducing costs and implementation time.

Compliance with PCI-DSS and PA-DSS standards can be considered as the biggest benefit of the Semi-integration package. Since no sensitive card account data is sent to the POS application driving the semi-integrated terminal, businesses can reduce their PCI compliance scope and associated risks.

Semi-integration ensures that the payment process remains secure by keeping the sensitive data transmission separated from other systems. This means the merchant never has access to sensitive card data, and all receipt data is returned truncated from the terminal device to the POS application (Desktop) securely. This provides a control for the customer experience and thereby enhances their security and satisfaction.





Decline recovery that works silently – but pays off loudly.
FlexFactor targets the most frequent decline codes—giving your business a smart, pre-approved path to recovery.
Subscribe to our newsletter and never miss any tips, tricks and examples from our experts.